Showing posts with label malware. Show all posts
Showing posts with label malware. Show all posts
Monday, March 27, 2017
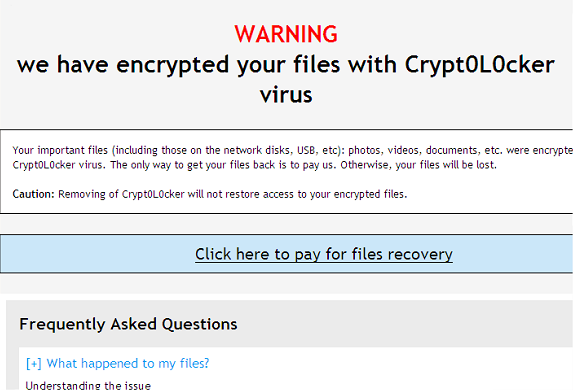
Encrypted Files encrypted extension Malware Removal Guide
Encrypted Files encrypted extension Malware Removal Guide
If all your files are encrypted with an .encrypted extension then your computer is infected with the Crypt0L0cker ransomware. Its very similar to the CryptoLocker but encrypts files in a slightly different way. It basically scans your computer and encrypts any files that do not match an exclude list (a list of files that cyber criminals think could cause a problem with Windows, mostly system files). Once a file is encrypted this ransomware appends the .encrypted extension to the file name, so for example your Word document becomes project.docx.encrypted instead of just project.docx. The same thing happens to all other files that are encrypted. They become inaccessible and you cant just simply decrypt them because Crypt0L0cker uses a rather sophisticated and strong encryption algorithm. When a file is encrypted it will append the .encrypted extension to the file name.
The majority of people working or playing with computers have heard of a good number of the assorted malicious software programs that are out there. We all know the threat of Trojan Horses, the sinister tactics of Spyware, the aggravating Adware and the pest that is Potentially Unwanted Programs, and lets not forget vicious viruses. However there is one type of malware that never seems to garner the same levels of notoriety as its cousins, and that is something named Ransomware. So what exactly is Crypt0L0cker ransomware and is it something that you should be overly concerned about if its not as well known? In a word: yes. Crypt0L0cker most definitely IS something you should know a little more about, and do your utmost to protect yourself from.
Here we are going to take a closer look at what ransomware is, how it spreads itself, what it can do to your files and PC - and more importantly - how you protect yourself from becoming a victim.
How does ransomware take control of your PC?
The Crypt0L0cker (.encrypted) ransomware is spread in a number of different ways; all of them seemingly innocuous, and therefore increasing the chances of us falling prey to the malware. Sometimes this ransomware is disseminated by email attachments or in links in mails or instant messages. Just a few days ago the AFP warned about AFP traffic infringement scam that distributed this ransomware.

The Trojan dropper is detected as TR/Crypt.Xpack.197573, Trj/RansomCrypt.C and Win32:Crypt-SAR [Trj]. Some users got caught by this virus campaign and immediately noticed that all jpeg, pdf and doc files had the extension ".encrypted" after them. Other variants of this ransomware are unleashed by programs or even entire websites that have been infected by it. So what do you need to do to lower your likelihood of being attacked? You need to be careful when opening emails and instant messages – especially if you dont know the sender – and of course you should exercise extreme caution when opening attachments, images, files or links within them. You also need to be very careful when downloading apps or programs in case they have been compromised. Its hard to say that you should also watch what websites you visit, as any site can be targeted by malware but the general rule of thumb is to avoid anything that your instincts tell you is low quality or contains dubious content.
What is Crypt0L0ckers MO?
Ransomware, as you may have already guessed, exists to extract money from you in the form of a ransom. And to do this it needs to hold something hostage, in this case, your computer.
A ransomware attack paralyses your operating system, leaving you unable to open files or programs. When you try, youll be hit with a ransom note sent by email or displayed on your screen telling you that you have been found to have downloaded illegal or pirated software or accessed a website of an illicit nature. It then demands a sum of money in return for the release of your documents or system.
Even worse, some ransomware will tell you that you are now on a watch list and about to be investigated for your alleged cyber crimes by the government or police! Clearly this is to convince you to pay the ransom, however, dont give in, but follow the steps in the removal guide below. First, you should remove the ransomware and any other related malware from your computer. Secondly, dont pay the ransom and try to restore your files with the tools listed below. If you back up your files regularly, you can retrieve some of your information, if not all of it, if your files suddenly become encrypted and have this odd *.encrypted extension. If you dont have any backups then you can try to restore at least some of your files with Shadow Explorer and other Windows system tools. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing Crypt0L0cker (.encrypted) and related malware:
Before restoring your files from shadow copies, make sure Crypt0L0cker virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.

2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Crypt0L0cker (.encrypted) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
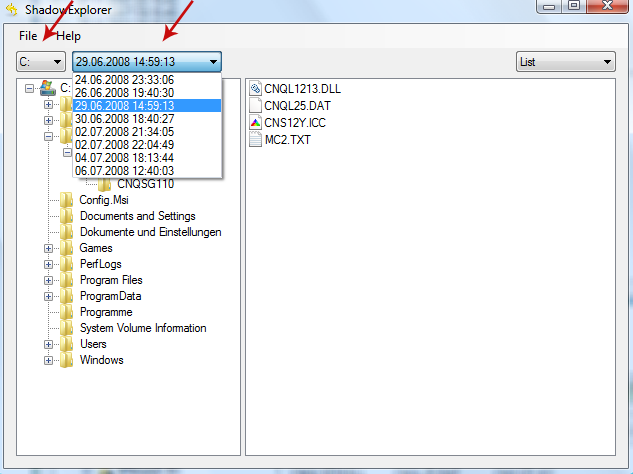
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
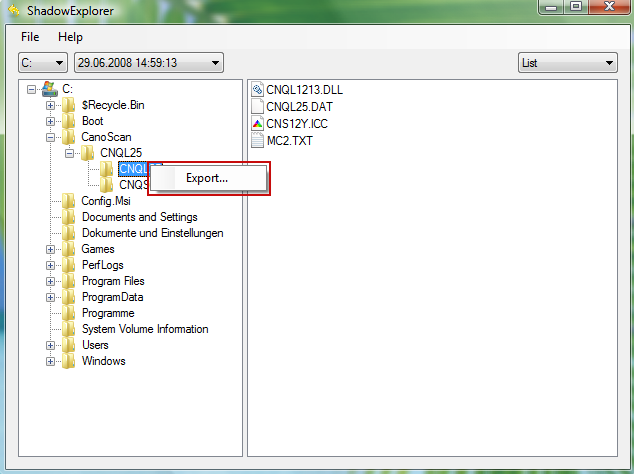
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download
Saturday, February 18, 2017
Fix Unable to connect to the proxy server Chrome Error Caused by Malware
Fix Unable to connect to the proxy server Chrome Error Caused by Malware
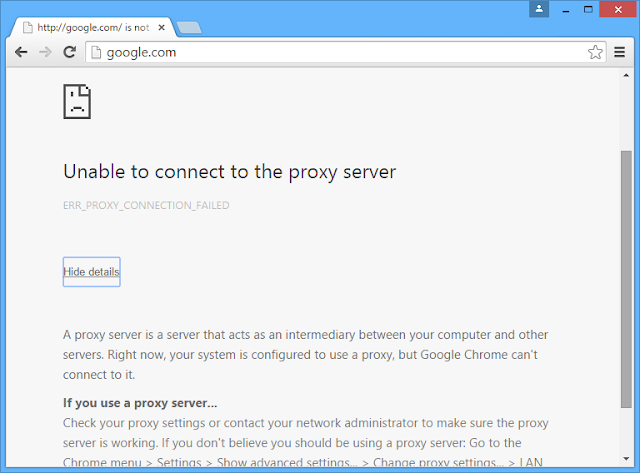
Due to the fact that you are reading this article, I can probably safely assume that you have unfortunately found it necessary to find out more about the "Unable to connect to the proxy server" Chrome error and learn how to fix it. I say unfortunately however, in truth, it is far better to be prepared and know your enemy than not. It is really just unfortunate that we are in this position in the first place. But we are, and from viruses to worms, and from phishing scams to social engineering, and of course not forgetting our old friend, malware, we are faced with no easy task if we want to keep our computers and other web-enabled devices free from harm. Google Chrome displays Unable to connect to the proxy server error message when it cannot connect to a proxy server (ERR_PROXY_CONNECTION_FAILED).
If you configured your web browser to use a proxy server yourself then its not a big deal, you just need to change your LAN settings back to default and youre good to go. But what if a malicious program changed it in order to hijack your web browser and redirect your web traffic through web servers controlled by cyber criminals? In that case, you will have to use a few tools and anti-malware software to remove the malware first and then reset malicious proxy settings. However, the problem is that most of the time malware wont allow you to reset proxy settings. Proxy server settings will be grayed out. Its called the ProxyOverride Trojan horse. As soon as you change your LAN settings back to normal this Trojan runs a script and reverts everything back to the previous state.
It doesnt really help that the malware and online scamming business is exactly that – business – and big business at that. Threats are increasing almost daily and the sheer variety of viruses and malware programs mean that we need to be constantly on top of things, and that includes ensuring your security software is as up to date as it can be. Im sure you all know spyware and keyloggers that are designed to steal your passwords and other sensitive information. But ProxyOverride Trojan horse that basically leaves you without internet access when web servers controlled by cyber criminals go down is also a dangerous infection. They can spy on you and gather various information which can be used later to organize a very specific cyber attack against you or even entire company. Its not a joke, if you keep getting this error message its time to scan your computer for malware.
In addition to this, whether you are a home computer user or the owner or manager of a small business, in order to defend yourself against Proxy Overriding, you need to stay as knowledgeable as you possibly can be when it comes to learning about all the latest threats you face every time you are using the internet.
One of those threats is something called ProxyOverride Trojan Horse
It works hard to take advantage of our trusting natures and even if you think that your personal online security habits cant be improved upon, take it from us; They can fool even the most security conscious. For example, when you see a pop up window on your screen that says you are infected by a virus, what is the first thing that springs to mind? Probably: Oh no – how do I get rid of this? And that is precisely where a Trojan Horse will take advantage of this loophole in your train of thought. Rather than being a helpful warning telling you that you need to rid your computer of this virus, the very same pop up window could in fact be a Trojan Horse in disguise.
How do you know if you are looking at the ProxyOverride?
Due to its duplicitous nature this is sadly easier said than done. It sometimes appears as pop up windows (usually left behind by a previous malware infection) or they can be hidden in downloads – such as a file or an app. Other types of Trojan Horse malware use the trusty old email attachment method.
What does ProxyOverride Trojan do?
It sets up a proxy server and hijacks your web browser. As a result, you may constantly get "Unable to connect to the proxy server" error message when using Chrome and other web browser. The absolute worst thing itcan do is to corrupt your files and data, rendering them inaccessible. On top of this, they can also cause your operating system to become unstable, and therefore more insecure. They can also corrupt your hard drive. The key is to never take anything at face value and if a program or app is begging you to download, ask yourself why.
How do I fix "Unable to connect to the proxy server" error and remove ProxyOverride Trojan horse?
You can definitely fix the problem yourself. First of all, you need to restart your computer in Safe Mode and remove ProxyEnable ProxySever registry keys using RegEdit program. Secondly, run a full system scan with recommend anti-malware software. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Fixing "Unable to connect to the proxy server" Chrome error and restoring Internet connection:
1. Restart your computer in Safe Mode. If you dont know how to do that, please watch this video.
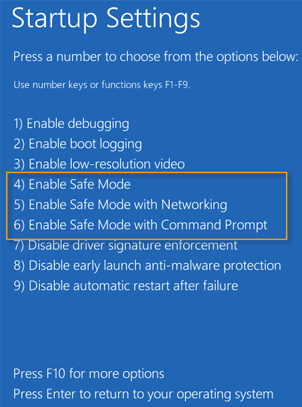
2. Open Windows Registry Editor. If you are using Windows 7 or older version click Start ? Run. Type in regedit and hit enter.
If you are using Windows 8 and later, please watch this video.
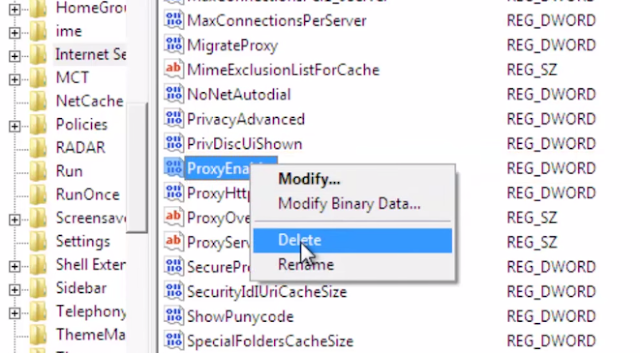
3. Navigate to HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionInternet Settings.
In the right-side pane select ProxyEnable key and delete it.
Then select ProxySever registry key and delete it too.
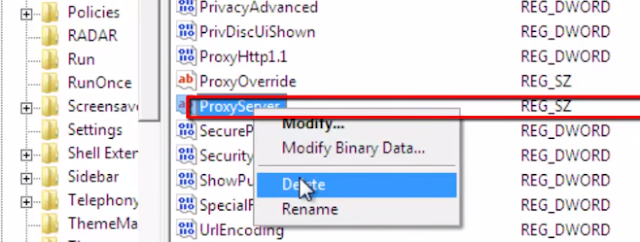
4. Navigate to HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRun.
In the right-side pane there should be only one registry key (Default). If you found another randomly named key and if it points to Temp or AppData folders, delete it.
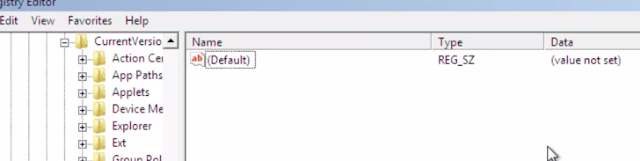
Thats it! Restart your computer in Normal Mode. Proceed to Step 2.
Step 2: Removing ProxyOverride Trojan horse and related malware:
1. Download anti-malware software and run a full system scan. It will detect and remove this infection from your computer.
2. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.

3. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.

Available link for download
Monday, December 5, 2016
Download Malwarebytes Anti Malware Premium 2 2 0 1024 Final With Serial Key
Download Malwarebytes Anti Malware Premium 2 2 0 1024 Final With Serial Key

Malwarebytes Anti-Malware is a high performance anti-malware
application that thoroughly removes even the most advanced malware and spyware. With one of the fastest, most effective quick scans and malware removal capabilities on the market, this program is the perfect addition to your PCs defenses.
The full version of the product includes a number of key features, including the ability to schedule updates and scans and most importantly, a real-time malware protection module that blocks malicious processes before they even start.
Whats New:
Improvements:
• Full support for Windows 10 operating system added
• Enhanced safeguards to prevent false positives on legitimate files
• Improved rootkit scanning to prevent false positives for Unknown.Rootkit.Driver and Unknown.Rootkit.VBR
• Minor user interface edits including updated Scan Results view and updated top navigation menu
• Added ability to sort the columns in Quarantine table under History tab
• Improved handling of scheduled updates set to run on reboot to prevent repeated missed updates
• Improved messaging in limited user accounts when an action requiring Admin privileges is attempted
• New message added when Malwarebytes Anti-Malware is running in a business environment
• Updated License Agreement included
Issues Fixed:
• Fixed security vulnerability and enhanced Malwarebytes Anti-Malware self-protection
• Fixed several issues related to updating databases in a limited user account
• Fixed issue where USB drives would not show as available for scanning on the Custom Scan Configuration screen
• Fixed several licensing issues that could potentially cause invalid license and protection states
• Fixed problem where double-clicking the tray icon would not launch the user interface
application that thoroughly removes even the most advanced malware and spyware. With one of the fastest, most effective quick scans and malware removal capabilities on the market, this program is the perfect addition to your PCs defenses.
The full version of the product includes a number of key features, including the ability to schedule updates and scans and most importantly, a real-time malware protection module that blocks malicious processes before they even start.
Whats New:
Improvements:
• Full support for Windows 10 operating system added
• Enhanced safeguards to prevent false positives on legitimate files
• Improved rootkit scanning to prevent false positives for Unknown.Rootkit.Driver and Unknown.Rootkit.VBR
• Minor user interface edits including updated Scan Results view and updated top navigation menu
• Added ability to sort the columns in Quarantine table under History tab
• Improved handling of scheduled updates set to run on reboot to prevent repeated missed updates
• Improved messaging in limited user accounts when an action requiring Admin privileges is attempted
• New message added when Malwarebytes Anti-Malware is running in a business environment
• Updated License Agreement included
Issues Fixed:
• Fixed security vulnerability and enhanced Malwarebytes Anti-Malware self-protection
• Fixed several issues related to updating databases in a limited user account
• Fixed issue where USB drives would not show as available for scanning on the Custom Scan Configuration screen
• Fixed several licensing issues that could potentially cause invalid license and protection states
• Fixed problem where double-clicking the tray icon would not launch the user interface
Home Page - https://www.malwarebytes.org/


INSTALL NOTES
(1): Download Malwarebytes Anti-Malware
(2): run the setup
(3): Use the Keygen To Activate
(4): Enjoy and Support Developers, Buy It, They Deserved It!
(1): Download Malwarebytes Anti-Malware
(2): run the setup
(3): Use the Keygen To Activate
(4): Enjoy and Support Developers, Buy It, They Deserved It!
Malwarebytes Anti-Malware Premium 2.2.0.1024 Final (21.84 MB)
Malwarebytes Anti-Malware Premium 2.2.0.1024 Final Keygen (79.05 KB)
Malwarebytes Anti-Malware Premium 2.2.0.1024 Final Keygen (79.05 KB)

Download Now ( 100% Working Link )
Available link for download
Sunday, October 2, 2016
Encrypted Files ezz extension Malware Removal Guide
Encrypted Files ezz extension Malware Removal Guide
If most of your files are encrypted and have a .ezz extension, for example docname.docx.ezz or image.jpg.ezz then your computer is almost certainly infected with the Alpha Crypt ransomware. Its a new veriant of the TeslaCrypt ransomware. Obviously, encrypted files cannot be opened by the standard program. They must be decrypted first but the problem is that you need to purchase your private key using Alpha Crypt service (AlphaTool Decryption Service) in order to do so. The fact that malicious software exists, and exists purely to do us harm, is yesterdays news. We all know about the proliferation of the various types of malware from spyware and Trojan Horses to Potentially Unwanted Programs and adware, but the one thing that we do need to be aware of is the fact that malicious software is in a constant state of self-improvement. If improvement is the right word to use! And that means that we need to educate ourselves about the latest programs if we are to arm ourselves with the best defense against attack.
With that in mind, Im going to take a closer look at ransomware that encrypts your files and append the .ezz extension to them; an unpleasant type of malware that is definitely an inhabitant of the more viscous end of the malware scale.
What does Alpha Crypt do?
Well were giving no prizes away for guessing and the clue is most definitely in the name here as ransomware has been designed to hijack, or kidnap your files or data and render them unusable. It then sends you a ransom note HELP_TO_SAVE_FILES.txt which demands payment for the release of the files. You will be paying for a code which purports to be the key to unlocking the encrypted data. However, take any promises to send you this code with a bucket load of salt. Many ransomware programmers simply take the money and run, which shouldnt come as any great surprise, considering the people were dealing with here! Alpha Crypt can be no exception.
How does ransomware send you a ransom note?
A ransom letter in the malware world wont be carefully cut out letters from newspapers like in the films of our youth (depending on how old you are!) but will be sent via an email or displayed on your screen. Some ransom notes are pop-up windows, others, rather menacingly take over your entire screen. This ransomware simply drops multiple HELP_TO_SAVE_FILES.txt files in folders where at least one file was encrypted. It also changes desktop background to HELP_TO_SAVE_FILES.bmp which displays the same ransom note as in the text file.
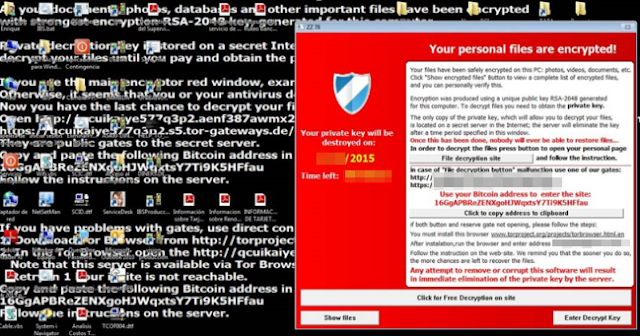
And just to add to the panic that youre no doubt experiencing since finding your computer in lock down mode, ransom notes amp up the fear factor in order to get you to pay quickly by telling you that the code will be invalid and youll never be able to retrieve your files if you dont pay by a certain date (usually within 3 days).
But hold on, as it gets worse. Some types of ransomware design the note to look as if it was sent by the FBI, CIA or other law enforcement or government agency. The note will explain, in no uncertain terms, that you are being investigated due to your habit of visiting suspicious websites or illegally downloading programs. Even if you KNOW you havent been on any websites supporting terrorism or download explicit images, the worry is still there. Did you accidentally click a link that you didnt mean to? Did someone else use your computer? Does the FBI know about that episode of The Walking Dead that you downloaded last week?
So now what? Should you make the problem go away by paying the ransom? The answer is most emphatically no. Do not encourage these online scammers. If you have a recent backup, wipe your hard disk and reinstall your files. If you dont, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .ezz. You can also use TeslaCrypt Decryption Tool by Cisco. It might just work with Alpha Crypt as well. But before restoring your files, please remove the ransomware and related malware files from your computer. Otherwise, you will simply waste your time. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing Alpha Crypt and related malware:
Before restoring your files from shadow copies, make sure Alpha Crypt is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.

Important! If you cant download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Alpha Crypt virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Try the TeslaCrypt Decryption Tool by Cisco. Download TeslaDecrypt tool and run it.
Method 4: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.

3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.

Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download
Subscribe to:
Posts (Atom)