Showing posts with label extension. Show all posts
Showing posts with label extension. Show all posts
Monday, March 27, 2017
Encrypted Files encrypted extension Malware Removal Guide
Encrypted Files encrypted extension Malware Removal Guide
If all your files are encrypted with an .encrypted extension then your computer is infected with the Crypt0L0cker ransomware. Its very similar to the CryptoLocker but encrypts files in a slightly different way. It basically scans your computer and encrypts any files that do not match an exclude list (a list of files that cyber criminals think could cause a problem with Windows, mostly system files). Once a file is encrypted this ransomware appends the .encrypted extension to the file name, so for example your Word document becomes project.docx.encrypted instead of just project.docx. The same thing happens to all other files that are encrypted. They become inaccessible and you cant just simply decrypt them because Crypt0L0cker uses a rather sophisticated and strong encryption algorithm. When a file is encrypted it will append the .encrypted extension to the file name.
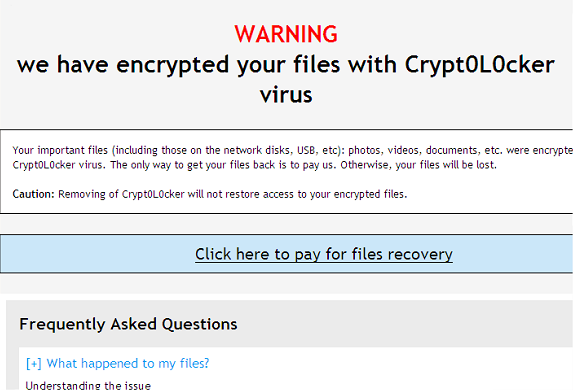
The majority of people working or playing with computers have heard of a good number of the assorted malicious software programs that are out there. We all know the threat of Trojan Horses, the sinister tactics of Spyware, the aggravating Adware and the pest that is Potentially Unwanted Programs, and lets not forget vicious viruses. However there is one type of malware that never seems to garner the same levels of notoriety as its cousins, and that is something named Ransomware. So what exactly is Crypt0L0cker ransomware and is it something that you should be overly concerned about if its not as well known? In a word: yes. Crypt0L0cker most definitely IS something you should know a little more about, and do your utmost to protect yourself from.
Here we are going to take a closer look at what ransomware is, how it spreads itself, what it can do to your files and PC - and more importantly - how you protect yourself from becoming a victim.
How does ransomware take control of your PC?
The Crypt0L0cker (.encrypted) ransomware is spread in a number of different ways; all of them seemingly innocuous, and therefore increasing the chances of us falling prey to the malware. Sometimes this ransomware is disseminated by email attachments or in links in mails or instant messages. Just a few days ago the AFP warned about AFP traffic infringement scam that distributed this ransomware.

The Trojan dropper is detected as TR/Crypt.Xpack.197573, Trj/RansomCrypt.C and Win32:Crypt-SAR [Trj]. Some users got caught by this virus campaign and immediately noticed that all jpeg, pdf and doc files had the extension ".encrypted" after them. Other variants of this ransomware are unleashed by programs or even entire websites that have been infected by it. So what do you need to do to lower your likelihood of being attacked? You need to be careful when opening emails and instant messages – especially if you dont know the sender – and of course you should exercise extreme caution when opening attachments, images, files or links within them. You also need to be very careful when downloading apps or programs in case they have been compromised. Its hard to say that you should also watch what websites you visit, as any site can be targeted by malware but the general rule of thumb is to avoid anything that your instincts tell you is low quality or contains dubious content.
What is Crypt0L0ckers MO?
Ransomware, as you may have already guessed, exists to extract money from you in the form of a ransom. And to do this it needs to hold something hostage, in this case, your computer.
A ransomware attack paralyses your operating system, leaving you unable to open files or programs. When you try, youll be hit with a ransom note sent by email or displayed on your screen telling you that you have been found to have downloaded illegal or pirated software or accessed a website of an illicit nature. It then demands a sum of money in return for the release of your documents or system.
Even worse, some ransomware will tell you that you are now on a watch list and about to be investigated for your alleged cyber crimes by the government or police! Clearly this is to convince you to pay the ransom, however, dont give in, but follow the steps in the removal guide below. First, you should remove the ransomware and any other related malware from your computer. Secondly, dont pay the ransom and try to restore your files with the tools listed below. If you back up your files regularly, you can retrieve some of your information, if not all of it, if your files suddenly become encrypted and have this odd *.encrypted extension. If you dont have any backups then you can try to restore at least some of your files with Shadow Explorer and other Windows system tools. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing Crypt0L0cker (.encrypted) and related malware:
Before restoring your files from shadow copies, make sure Crypt0L0cker virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.

2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Crypt0L0cker (.encrypted) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
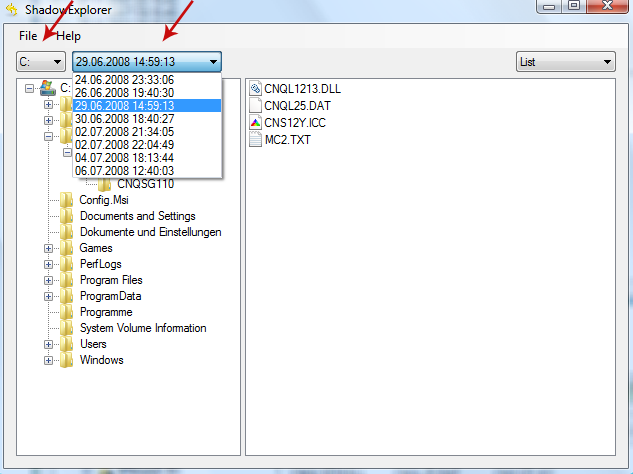
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
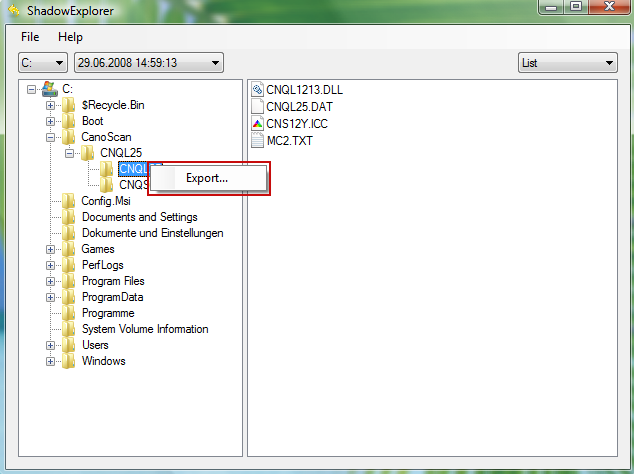
Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download
Wednesday, March 15, 2017
CryptoWall aaa Extension Ransomware Removal Guide
CryptoWall aaa Extension Ransomware Removal Guide
A new variant of CryptoWall 3.0 ransomware not only encrypts your files but also appends .aaa after the original file name and extension, for example report.docx.aaa or statistics.xls.aaa. This new variant also drops slight modified ransom notes restore_files_hprjq.html and restore_files_hprjq.txt files in each folder where at least one file has been encrypted.
What is CryptoWall ransomware?
There are a few different ways that CryptoWall 3.0 is spread. It may be attached as a file or link in an email or instant messenger chat. It can infect you via a drive by installation which is when you visit a website that was compromised by ransomware. Or you might have downloaded a program or app which was pre-infected. All of these methods are things that can affect each and every one of us, which is why you need to know what ransomware can do – and then take more care when youre online, whether youre checking email or downloading files.

What does CryptoWall do once its infected your computer?
It isnt shy and retiring and it wont hide in the shadows, running on your PC without your knowledge while it does its damage. You will know pretty much straight away once you have been infected by it. Ransomwares trick is to kidnap your files so that you cant access them, and then demand that you pay a ransom to be given access to them again. The CryptoWall 3.0 usually encrypts the files and tells you it will send you a code to decrypt them once you have paid up. This particular variant also appends .aaa extension to the encrypted files and displays modified ransom note. Content of the restore_files_hprjq.txt ransom note:
______!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!______________
What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall 3.0.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them,
it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 - public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
But one of the scariest things about CryptoWall 3.0 ransomware is the way in which it presents its demands for money. First of all youll be sent an email or shown a pop up window telling you that youve been caught looking at illicit web content or illegally downloading files, which is why you files have been locked. It will tell you that once youve paid a fine to atone for this misbehavior, your files will be unlocked, or youll be sent the decryption code.
A word of warning: this is a scammer you are dealing with here and there are countless stories about people paying the ransom only to not hear another word and be left with encrypted and inaccessible files.
Protect yourself from ransomware
Do your best to avoid this stressful – and potentially expensive – scenario and install some reputable security software today. Also, backup your files at least once a week. Doing so will certainly safe you time, money and headaches.
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you dont, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .aaa. But before restoring your files, please remove the ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing CryptoWall 3.0 ransomware and related malware:
Before restoring your files from shadow copies, make sure the CryptoWall is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.

Important! If you cant download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by CryptoWall 3.0 virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.

3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.

Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download
Labels:
aaa,
cryptowall,
extension,
guide,
ransomware,
removal
Wednesday, January 25, 2017
Encrypted Files zzz extension Ransomware Removal Guide
Encrypted Files zzz extension Ransomware Removal Guide
A virus appended all files with .zzz extension? Unfortunately, your computer is infected with a variant of Alpha Crypt ransomware. Some users reported that they got a ransom note "restore_files_qfprl.txt" saying its the CryptoWall 3.0 ransomware once their files were encrypted and extensions changed to .zzz. However, I dont think its true simply because this particular ransom virus does not remove shadow copies whereas CryptoWall 3.0 does remove shadow copies and even takes the extra step by removing original files from mapped network drives. Whether youre an individual home user, a small business or running a large enterprise, none of us are immune to this ransomware attack. And the worrying part is that most hackers, attackers and malware users choose to target the easy option – so that means you or me on our home computers, and small or medium sized businesses.
A closer look at crypto-virus that adds a file extension .zzz to all files
Okay, Im going to take a wild guess and assume that you are not at great risk of being kidnapped. Well, not personally that is - but what about your computer? Ransomware can, and will if you are unlucky enough to be infected, hijack your operating system and hold your files and documents to ransom. Let’s take a closer look at what it can do. One of the new kids on the malware block and a program that you do need to be aware of is something called ransomware. This thoroughly unpleasant software can have a not inconsiderable financial impact on you and can also result in a great deal of stress as well. This ransomware infects you during a drive-by installation, meaning that it downloads itself onto your PC instantly if you have visited a compromised website. This will set into motion a string of decidedly unfortunate events. Unbeknown to you, youve visited this infected website, you carry on browsing the web, and the next thing you know is that your computer has frozen. Most of the time, it comes packed with Trojan downloaders and Trojan droppers that are distributed via infected websites using various exploit kits. It also comes as an email attachment, so be very careful when opening attached files even from people you know.
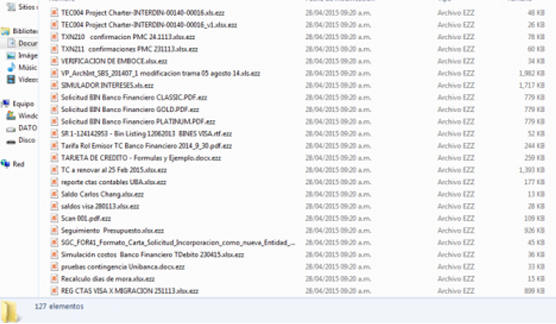
Once installed, it will search your computer for all data files and encrypt them using RSA-2048 crypto algorithm. Its a very strong algorithm which cant be brute forced or braked in any other way unless you have a super computer at home. What makes this ransom virus unique is that it adds a file extension .zzz to all encrypted files. For example, if your original file is resume.doc it becomes resume.doc.zzz. Encrypted files can not be decrypted or opened by any other program than the decryptor tool created by cyber criminals who created this virus. In order to get the decryptor you need to pay the ransom, usually $300 or even more.
How to react to .zzz ransomware
It can be tempting to throw money at the problem to make it go away and to unlock your PC. But thats the wrong move – whether youve accessed sites of a disreputable nature or not. For a start, no law enforcement agency would act in this way – so do not even think that you should pay anything. If you do you are simply creating a snowball effect by buying into a fraudulent operation and showing these people that crime does pay. Seek help from a professional repair person or use the removal guide below.
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you dont, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .zzz. But before restoring your files, please remove the ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing .zzz extension ransomware and related malware:
Before restoring your files from shadow copies, make sure the ransomware is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you cant download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by .zzz extension virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.

3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.

Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download
Sunday, December 4, 2016
Files Encrypted crypt Extension Ransomware Removal Guide
Files Encrypted crypt Extension Ransomware Removal Guide
Files with .crypt extension are encrypted by ransomware from the Ransom:Win32/Troldesh family. In case you are wondering why all your files have "CRYPT" file format and you cant open them I have bad news for you - your computer is infected with ransomware. This particular ransom virus encrypts files and inserts contact information in a file name, for example !____________DESKRYPTEDN81@GMAIL.COM.crypt or !helpfiledeskript111@gmail.com.crypt. Cyber criminals give email addresses (yours might be different) and hope that you will contact them to get further information on how to decrypt your files. Thanks to our lives virtually being played out online, cyber criminals have a whole host of people to choose from to scam, phish, extort, scare and wreak havoc upon. They also employ increasingly sophisticated methods to con us out of our data, identity and money. And the myriad of applications, files, tools and programs that we are constantly downloading means they have even more ways to infiltrate our computers.
Why you need to be aware of .crypt ransomware
It is a type of malicious software that you really need to be aware of. Unlike some malware which only has one line of attack, ransomware can have a very real and detrimental effect on you thanks to its modus operandi which is to not only cause mayhem on your computer and to your files, but also to attempt to extort money from you. So how does this ransom virus infect you and what does it actually do to you and your computer?
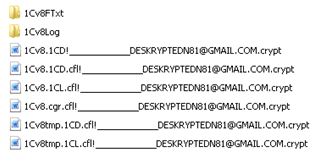
Ransomwares MO
In a nutshell, it infects your computer, encrypts your files, appends .crypt extension, inserts contact information and holds your files or data to ransom and then demands a sum of money from you in lieu of their release.
What will likely happen is that while youre using your computer it will suddenly freeze and an on-screen message will appear telling you that you have been hijacked. And if that wasnt panic inducing enough, many ransomware programs also make this ransom note look as if it has been sent either by your local police force or even from a government body such as the FBI. Official wording and logos will add additional authenticity dialling the fear factor up even further. So exactly WHY is the FBI holding your data hostage? The warning will tell you it is because you are guilty of visiting illegal or banned websites, or viewing or downloading illicit, pirated or sensitive files or content. Once the fine has been paid the FBI will unfreeze your PC. Of course, your ransom note can be completely different or the particular variant that you have on your computer may not even have a ransom note. Sometimes, an email address in a file name like DESKRYPTEDN81@GMAIL.COM.crypt is more than enough.
Obviously this would cause even the most level headed among us to at least momentarily panic. Is it possible that you might have accidentally visited a website with dubious content? What about that TV show you downloaded – was that an illegal act? Chances are you dont want to take any risks – or perhaps you have recently looked at an x-rated website and are embarrassed. Should you just pay the fine and be done with it? Absolutely not! Unless, of course, your files are very important and you cant afford losing them. But its always a good idea to try a few data recovery tools before paying the ransom.
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you dont, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .crypt. But before restoring your files, please remove the ransomware and related malware files from your computer. Otherwise, you will simply waste your time. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing .crypt extension ransomware and related malware:
Before restoring your files from shadow copies, make sure the ransomware is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you cant download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by .crypt extension virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Try the TeslaCrypt Decryption Tool by Cisco. Download TeslaDecrypt tool and run it.
Method 4: Try the TeslaDecoder Decryption Tool. Download TeslaDecoder tool and run it.
Method 5: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.

3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.

Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download
Sunday, October 2, 2016
Encrypted Files ezz extension Malware Removal Guide
Encrypted Files ezz extension Malware Removal Guide
If most of your files are encrypted and have a .ezz extension, for example docname.docx.ezz or image.jpg.ezz then your computer is almost certainly infected with the Alpha Crypt ransomware. Its a new veriant of the TeslaCrypt ransomware. Obviously, encrypted files cannot be opened by the standard program. They must be decrypted first but the problem is that you need to purchase your private key using Alpha Crypt service (AlphaTool Decryption Service) in order to do so. The fact that malicious software exists, and exists purely to do us harm, is yesterdays news. We all know about the proliferation of the various types of malware from spyware and Trojan Horses to Potentially Unwanted Programs and adware, but the one thing that we do need to be aware of is the fact that malicious software is in a constant state of self-improvement. If improvement is the right word to use! And that means that we need to educate ourselves about the latest programs if we are to arm ourselves with the best defense against attack.

With that in mind, Im going to take a closer look at ransomware that encrypts your files and append the .ezz extension to them; an unpleasant type of malware that is definitely an inhabitant of the more viscous end of the malware scale.
What does Alpha Crypt do?
Well were giving no prizes away for guessing and the clue is most definitely in the name here as ransomware has been designed to hijack, or kidnap your files or data and render them unusable. It then sends you a ransom note HELP_TO_SAVE_FILES.txt which demands payment for the release of the files. You will be paying for a code which purports to be the key to unlocking the encrypted data. However, take any promises to send you this code with a bucket load of salt. Many ransomware programmers simply take the money and run, which shouldnt come as any great surprise, considering the people were dealing with here! Alpha Crypt can be no exception.
How does ransomware send you a ransom note?
A ransom letter in the malware world wont be carefully cut out letters from newspapers like in the films of our youth (depending on how old you are!) but will be sent via an email or displayed on your screen. Some ransom notes are pop-up windows, others, rather menacingly take over your entire screen. This ransomware simply drops multiple HELP_TO_SAVE_FILES.txt files in folders where at least one file was encrypted. It also changes desktop background to HELP_TO_SAVE_FILES.bmp which displays the same ransom note as in the text file.
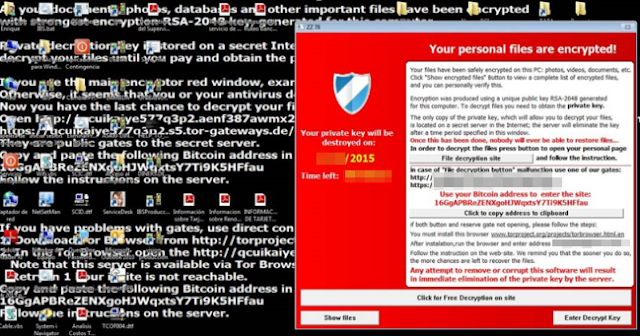
And just to add to the panic that youre no doubt experiencing since finding your computer in lock down mode, ransom notes amp up the fear factor in order to get you to pay quickly by telling you that the code will be invalid and youll never be able to retrieve your files if you dont pay by a certain date (usually within 3 days).
But hold on, as it gets worse. Some types of ransomware design the note to look as if it was sent by the FBI, CIA or other law enforcement or government agency. The note will explain, in no uncertain terms, that you are being investigated due to your habit of visiting suspicious websites or illegally downloading programs. Even if you KNOW you havent been on any websites supporting terrorism or download explicit images, the worry is still there. Did you accidentally click a link that you didnt mean to? Did someone else use your computer? Does the FBI know about that episode of The Walking Dead that you downloaded last week?
So now what? Should you make the problem go away by paying the ransom? The answer is most emphatically no. Do not encourage these online scammers. If you have a recent backup, wipe your hard disk and reinstall your files. If you dont, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .ezz. You can also use TeslaCrypt Decryption Tool by Cisco. It might just work with Alpha Crypt as well. But before restoring your files, please remove the ransomware and related malware files from your computer. Otherwise, you will simply waste your time. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing Alpha Crypt and related malware:
Before restoring your files from shadow copies, make sure Alpha Crypt is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.

Important! If you cant download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Alpha Crypt virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Try the TeslaCrypt Decryption Tool by Cisco. Download TeslaDecrypt tool and run it.
Method 4: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.

3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.

Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download
Subscribe to:
Posts (Atom)